What does it mean by adding a Security Group ID as a source in another Security Group ?
Let's uncover this small mystery once and for all about adding a Security Group in another Security Group!
Table of contents
At some places like Documentation and Tutorials, I have seen that In the source of a rule in the Security Group, they add another security group which seems weird 🤔
Attached a screenshot below :
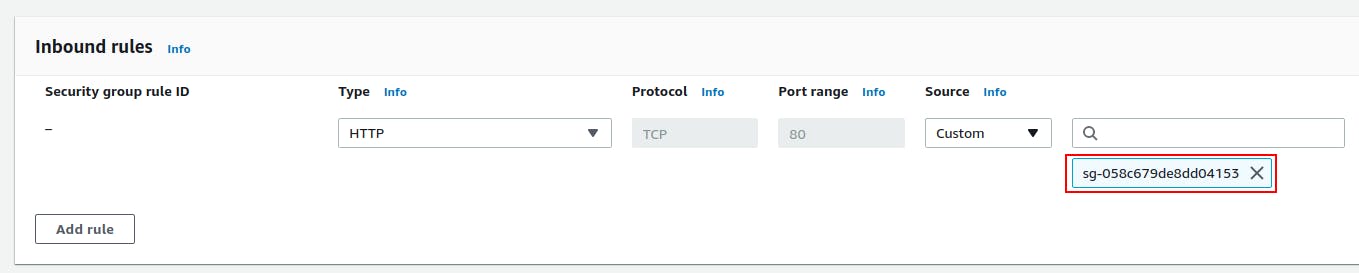
Okay, so this was pretty difficult for me to understand initially😅 and I was kind of misunderstanding this, So let's clear some air and improve our basics.
Let's Start!

Have you ever seen this kind of Security Group Configuration?
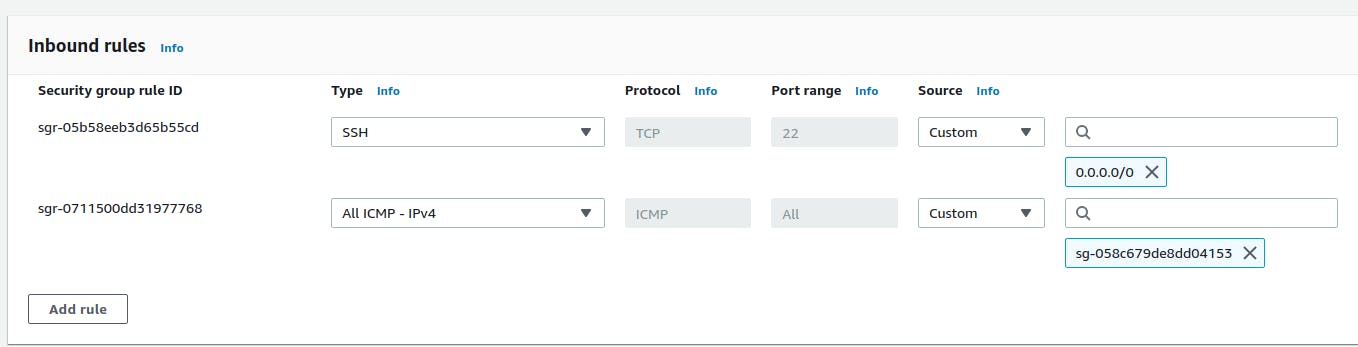
Notice the second rule in the SG Inbound rules!
Explaination
It simply means that " allow the traffic coming from all the members attached to that Security Group(which we added as the source in that particular rule)"
- Members means the instances(or other resources which uses a network interface)
- Remember! - Here it points the Private IPs of those Members
Use cases
In the case of ELB and EC2s, you can create 2 Security Groups, one for EC2s and one for Load Balancer. Now, In the EC2's Security Group, suppose your app runs at ports 80 and 443, create the inbound rules, and in the source for those rules add the Security Group ID of the Load Balancer's Security Group. That way you are only allowing traffic coming from Load Balancer, All direct traffic will be dropped!
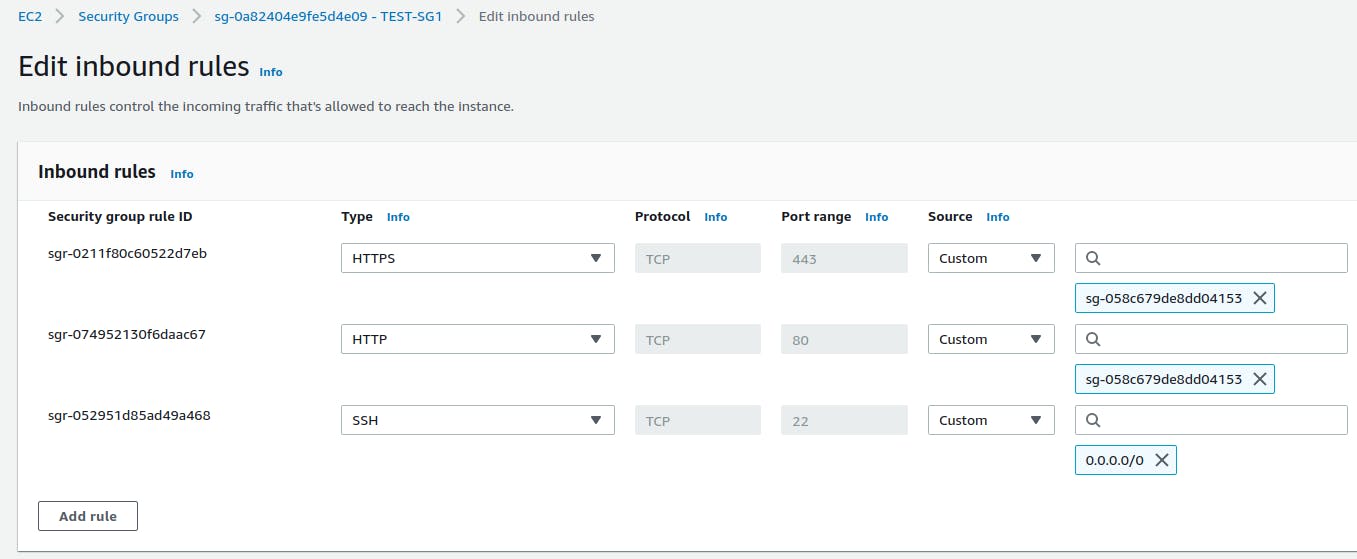
Suppose you have a few instances. Now, you want to allow all inter-instance communication b/w them.
One dumb and insecure approach can be :
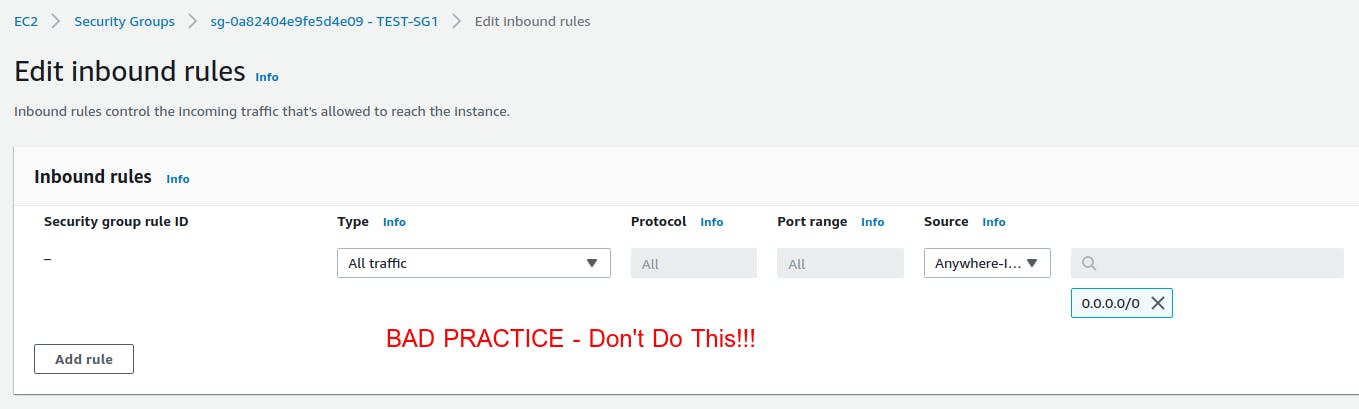
Here you allowed all Traffic from any source (0.0.0.0/0)
One other and better approach can be to use the concept, what we just learned.
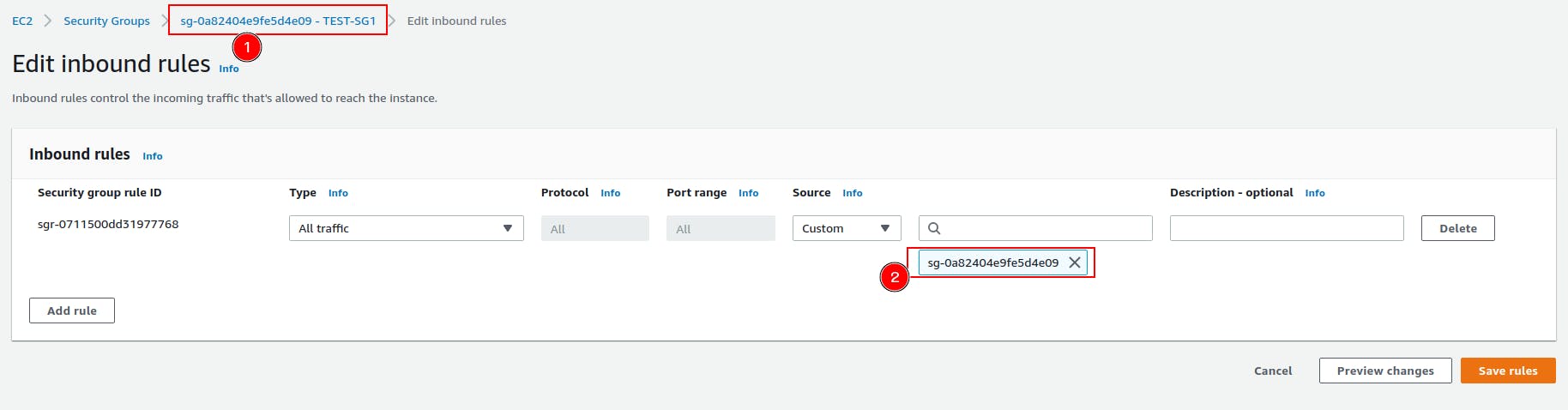 Here you can see we have given the ID of the Security Group itself.(Instead of giving 0.0.0.0/0)
This means --> All the member(who have this SG attached), will be able to connect to other members on any port.
Here you can see we have given the ID of the Security Group itself.(Instead of giving 0.0.0.0/0)
This means --> All the member(who have this SG attached), will be able to connect to other members on any port.
Note: Instead of all traffic, if you want, you can specify ports as well which are being used.
Private IP Addresses
From the Official Docs, "When you specify a security group as the source for a rule, traffic is allowed from the network interfaces that are associated with the source security group for the specified protocol and port. Incoming traffic is allowed based on the private IP addresses of the network interfaces that are associated with the source security group (and not the public IP or Elastic IP addresses).
- So when we are using this approach, keep in mind that behind the scenes it is whitelisting the private IPs of those Members!, So you won't be able to connect to the specified port if you are using Public or Elastic IP.
Hope you have learned something new from this blog :)
 If you have any Queries/Feedback, do let me know 🙏
If you have any Queries/Feedback, do let me know 🙏
Thank you so much!


